
Internet of Things Privacy Threats and Countermeasures
The Internet of Things is exciting for Makers, entrepreneurs, and consumers, but they’re not the only ones. Retailers, law enforcement agencies, and of course the Feds are also taking advantage of the combination of sensors, networked cameras, and connect
There are countless legal and social issues to be sorted out around surveillance and privacy. In the meantime, here are some of the IoT technologies that are pushing digital privacy concerns into the physical world — and some of the early ideas for circumventing them.
- Passive Phone Tracking
- Facial / Emotion Recognition
- Employee Tracking
- License Plate Readers / Vehicle Tracking
- Additional Resources
11/01/2019
Passive Phone Tracking

Sure, your phone has GPS, which means that your carrier, at least, always knows where you are. And that can actually be a blessing if your phone is lost or stolen. But we’re talking about a different kind of tracking here, one that operates on a much more localized scale -- and is also extremely easy to implement.
If your phone’s mapping app has ever suggested that it could pinpoint your location better with Wi-Fi enabled, you’re already familiar with this technique. Basically, it involves setting up one or more Wi-Fi routers and...well, actually, that’s about all it involves.
A cell phone is constantly checking around for available Wi-Fi networks. It does this by sending out a low-power signal, like a sonar ping, and then listening for responses. Like all data packets the phone sends, this ping is tagged with the phone’s MAC address -- a more-or-less unique identifier that helps the router tell one iPhone apart from another.
So even if a device isn’t connected to any Wi-Fi network, it’s still making itself visible to nearby routers with every ping. And that means whoever controls the routers can triangulate the location of a phone by watching for its MAC address as it moves from the range of one router to the next.
As surveillance goes, MAC address tracking isn’t terribly invasive. It doesn’t involve snooping on the content of your phone or your communications, and in public places it’s not usually reasonable to expect that the fact of your presence there is private information anyway. But this sort of tracking can feel very Big Brother and depending on how the data is shared very comprehensive in its scope.
For instance, advertising firm Renew London caused a public outcry last year when it was revealed that it’s digital billboards, embedded in recycling bins throughout the city, were recording MAC addresses -- and therefore cell phones, and therefore people -- as a way to measure the audience the ads were reaching.
According to a statement from Renew’s CEO, each billboard aggregated and anonymized the data by reporting only the total number of devices detected at a given time; the company claimed it couldn’t even tell whether a particular address was a repeat. But had they not done so, the same data could have been used to tell not only how many people passed each particular billboard, but also when, how many times, and in which sequence. That pattern would amount to 24-hour surveillance of everyone in downtown London.
Renew’s monitoring program was stopped in August, but others are springing up. Clark County, in Washington, is capturing MAC addresses over Bluetooth from the side of the highway to keep tabs on traffic flow. And in November, The Stranger reported that the Seattle Police Department had installed a mesh network that could, among other things, be used for exactly the kind of surveillance described above -- and that the city didn’t even have policies in place governing how such surveillance could be carried out, and who would have oversight.
With the recent accessibility of Bluetooth Beacons and indoor location technologies becoming much more accurate in their tracking expect this activity to increase dramatically in the coming years.
Countermeasure

Luckily, it’s easy enough to avoid MAC address tracking: just turn off Wi-Fi on your phone when you don’t need it, or take your Bluetooth settings out of “discoverable” mode. If that doesn’t set you at ease, a few groups have set out to create pouches made of conductive fabric to hold your phone, which acts as a Farraday cage and blocks all incoming and outgoing signals. You can order one readymade in a variety of sizes, or sew one yourself on the cheap.
Additional:
- In-Store Analytics companies
- Future of Privacy Forum - Smart Store Privacy
- Bluetooth Beacons / iBeacons: Estimote, Beekn
- Where the F**k Was I? (A Book) - James Bridle
- At Newark Airport, the Lights Are On, and They’re Watching You - NYTimes
Facial & Emotion Recognition
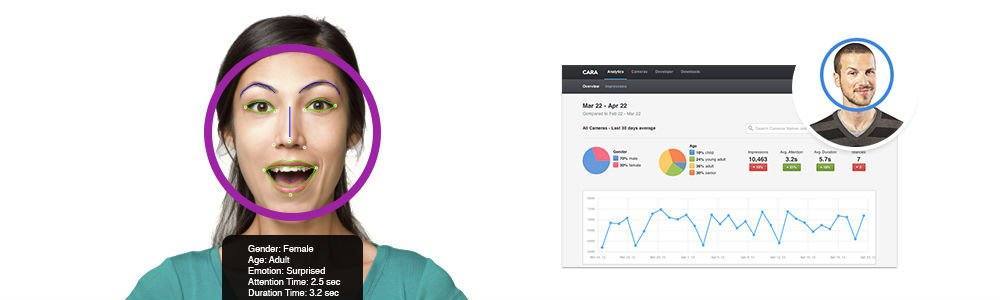
Again, yes: Facebook and photo-sharing sites do this already, and we welcome the convenience of not having to tag everybody ourselves. But are we equally comfortable when retailers and advertisers start to analyze our faces in real time, so they can try to influence and track our purchasing decisions, or having a passerby on the street identify you as they walk past you wearing their Heads-Up Display like Google Glass?
International snack giant Mondel?z is one of the companies exploring exactly these types of technologies in a retail environment by installing smart shelves near grocery check-out counters. The shelves will use cameras and face-recognition software to assess factors like the age and gender of nearby shoppers, and tailor the display to promote products that fit that person’s demographic. Tesco plans to roll out a similar system to all of its UK gas stations and it has already been used by Kraft as a way to dispense product samples out only to adults

Some companies take the creep factor even further: Almax now offers mannequins with cameras embedded right in their faces, so that the retail analytics software can stare back at you while you window-shop. Others focus on the dynamics of faces to decode shoppers’ emotional states. Systems like Facet andCara offer real-time analysis of micro expressions so companies can tell if their ads or products put people in a buying mood and do some A/B testing on their displays.
Facial recognition is a boon to law enforcement, of course, and the NYPD even has a special unit that focuses on matching security camera footage and mugshots with photos from Instagram and other social media. But as always, it’s a fine line between catching criminals and subjecting everyone to a surveillance state. For instance, one might wonder whether airports, which are already saturated with invasive security systems, really need the MFlow Journey facial-recognition system, which promises “to measure and improve the passenger journey; increas[e] dwell time and passenger spend in retail areas and [allow] greater operational control.”
Video cameras will also be enabled with the ability to passively capture biometric information, making it possible to actually "see" someone's heart rate as they walk by using standard video footage technology.
All of these, with the exception of law enforcement of course, claim that the faces they capture and analyze are anonymous, in the sense that the data they glean from your face isn’t matched with your real-world identity. At the moment this is driven by PR and policy decisions rather than around if it is technically possible to implement these systems.
Additional:
- Facial Substitution - Arturo Castro
- Computational Affective Video-in-Video Advertising - CAVVA (PDF)
- NEC VIP Detection
- FaceFirst
News:
- Japan vending machine recommends drinks to buyers - Reuters
- When No One Is Just a Face in the Crowd - NYTimes
Countermeasure

At CV Dazzle, artist Adam Harvey presents some tips for using extreme hairstyles and geometric, high-contrast makeup patterns to make your face undetectable by several state-of-the-art recognition systems (and many humans, too, no doubt). Creating asymmetry, covering an eye, and obscuring the place where the nose meets the brow can help keep you fashionably faceless.
On the other hand, you could just wrap your head in a scarf or wear a balaclava -- yours needn’t be pixellated -- but be aware that it’s illegal to wear full-face masks in some places.


Additional:
- FACE:REC - Howie Woo
- How to hide from machines - Dis Magazine
- Stealth Wear - Adam Harvey
Employee Tracking
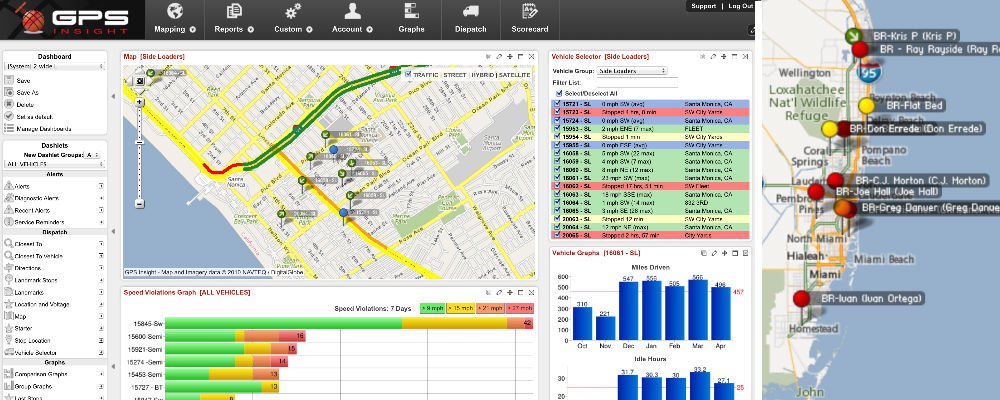
Consumers aren’t the only targets of surveillance technologies. Workers on the other side of the cash register, in the stockroom, or in the cabs of delivery vehicles can be subject to all manner of monitoring.
Tesco, for instance, allegedly has used digital armbands to monitor its warehouse employees for “efficiency.” Workers use the devices to scan the stock and keep track of shipments; meanwhile, the armbands track how long each task takes and grade the employees according to schedules set by management. Forget to log a bathroom break, or exceed the daily allotment of 25 minutes of break time, and scores drop. Former employees said the system put enormous pressure on the staff, many of whom are immigrants from Eastern Europe.
Meanwhile, GPS and telematics systems allows delivery drivers to find their way, but also lets employers keep tabs on them. Many truckers now use GPS jammers to block those signals. The devices are relatively simple and can cost as little as $50, but like anything that intentionally blocks legitimate communication signals, they are thoroughly illegal just about everywhere. And they can be dangerous, especially near airports. Last summer a man was fined nearly $32,000 for disrupting air traffic control signals at Newark Airport, just by driving past the airport with a GPS jammer active.
Ever since the industrial revolution and the invention of the punch clock, management types have used technology to make their workforces more robotic, more drone-like, in the pursuit of an ideal of “efficiency” that often bears little resemblance -- and pays little respect -- to human nature. Unfortunately, the Internet of Things is enabling a new chapter in this old story.
Additional:
- Hospital hand hygiene monitoring system
- Sociometric® Badge
- Tracking Sensors Invade the Workplace - WSJ
License Plate Readers / Vehicle Tracking

If it’s not enough that we’re being tracked at work and while out shopping, we are also increasingly surveilled in our cars. Police can now go far beyond speed traps and even red light cameras, by employing automated license plate readers along roads and highways. These devices can capture up to 1800 license plates per minute -- and what’s more, the data is often stored in large databases that can be linked across states.
The ACLU dug into this issue and found that, in effect, law enforcement agencies are building databases that can track the movements of millions of innocent Americans around the country. Data retention policies varied widely, from agencies that delete the data after just 48 hours (the Wisconsin State Police) to states that have no policy in place whatsoever, and can presumably save the data indefinitely (towns in Texas and California, among others).
Since license plates must be displayed, we know of no direct countermeasure to this technology -- except to ride a bike or take the bus.
Additional:
- You Are Being Tracked (PDF) - ACLU
- EU group mulls 'remote car-stopping device' for police - BBC
- Ford Research unveils heart rate monitor seats - Mobi Health
Art
The Walls Have Eyes was a sort of digital performance installation at last year’s Mozilla Festival (Mozfest) in London. It was developed by the BBC’s research and development wing and was one of several surveillance-based projects integrated with the Ethical Dilemma Cafe workshop and lounge space.
The Ethical Dilemma Cafe was a brick-and-mortar send-up of the End User License Agreements we all automatically click past when installing any new piece of software. A set of handwritten terms posted by the entrance made it clear that by walking into the cafe, Mozfest attendees were giving up their right to privacy, to control of their own data, and to ownership of all information created or exchanged in the space. In return, the cafe offered free smoothies and popcorn; very few people balked at the tradeoff.
One of the ways patron were surveilled was through The Walls Have Eyes — technically a misnomer, since the installation relied on picture frames to hide its spy gear. Each frame contained a Raspberry Pi with two Wi-Fi cards, a camera and a USB battery pack. One Wi-Fi card scanned for MAC addresses, the unique numerical tags that identify a particular device like a cell phone, tablet or laptop on a network. Meanwhile the camera snapped surreptitious photos, and the second Wi-Fi card transmitted the images and MAC data to a “hub” Pi hosting a private local network.
A refurbished dot-matrix printer noisily converted the photos and addresses into ASCII pictures — reams and reams of them, spilling from a balcony onto the ground floor. Cafe managers hung some of the printouts from clotheslines above the tables as a visual reminder of the constant, automatic churn of data collected about the patrons (the organizers called it “airing their dirty data”).

In most everyday settings, like stores and coffeeshops, MAC address tracking is usually invisible but no less constant than it was in the Ethical Dilemma Cafe. Our devices exchange the identifiers passively with nearby access points, which is necessary in order to discover and connect to Wi-Fi networks. But what happens to the data then is an open question.
Many retailers and advertisers have realized that MAC addresses provide a fairly reliable way to track individual customers, opening the possibility of targeted, location-based messages and offers. But the idea of marketers following their every move often makes consumers uncomfortable. Last year London had to stop an advertising company from conducting MAC address tracking with digital billboards attached to curbside recycling bins, after a public outcry.
Data collected at the Ethical Dilemma Cafe was always obfuscated, kept to a local private network, and deleted when Mozfest ended. But in the real world, the dilemma persists: How much access are we willing to give third parties to our devices and data, and what are we willing to accept in return?
You can view more details and dig into the operating code on the project’s Github page.
Where To Learn More?
Fighting digital surveillance is as much about changing the culture as anything else. Countermeasures are, in most cases, just a temporary or last-resort solution.
Here are some resources that can help you become more informed about surveillance technology, how it’s being used, and what you can do to influence the future of privacy.
- The ACLU has made privacy in the digital age one if its key issues. It provides resources about everything from cell phone tracking to license plate readers, and can connect you to opportunities for activism and civic engagement.
- The FTC is well aware of the Internet of Things, including the privacy concerns some IoT technology raises and is having hearings on the issue. The agency is an important regulator with the power to shape the future of privacy in many ways in response to input from lawmakers, industry, and the public. Already the agency has brought an Internet of things enforcement action against TRENDnet Inc. The company sells a video camera designed to allow consumers to monitor their homes remotely which settled with the commission in September 2013 that their security practices exposed hundreds of individuals lives to public viewing.
- The Future of Privacy Forum is a nonprofit think-tank that advocates for responsible data practices.
- Electronic Frontier Foundation (EFF)
"EFF is a donor-funded nonprofit and depends on your support to continue successfully defending your digital rights."
Websites:
- Websites like The Security Ledger and The New Aesthetic collect news about surveillance, privacy, and the Internet of Things from within their unique frames.
- Evgeny Morozov's Slate Column
Articles:
- The Networked Urban Environment - Jan Chipchase
- Personal Data: The Emergence of a New Asset Class - World Economic Forum
- Mining the Networked Self - Tal Z. Zarsky (PDF)
- Internet of Things: where is it heading? - Rob Van Kranenburg
- Internet of People, Things and Services - The Convergence of Security, Trust and Privacy (PDF) - Eloff, J.H.P., Eloff, M.M., Dlamini, M.T. & Zielinski M.P
- Surveillance and the Internet of Things - Bruce Schneier
- Who Really Believes in “Permissionless Innovation”? - Adam Thierer
Books:
- Against the Smart City - Adam Greenfield
- To Save Everything, Click Here - Evgeny Morozov
- Who Owns the Future? - Jaron Lanier
- Adversarial Design - Carl DiSalvo
- Configuring the Networked Self: Law, Code, and the Play of Everyday Practice - Julie E. Cohen
- Welcome to the Machine: Science, Surveillance, and the Culture of Control - Derrick Jensen, George Draffan
- The Transparent Society: Will Technology Force Us To Choose Between Privacy And Freedom? - David Brin

